ZTA adds high standards of data security, but can be exploited to bring down an entire enterprise network
when under a DDoS attack. Here is what you need to know to keep your network secure and available.
In this article we will explain how Zero Trust is now the highest priority for organizational security and its challenges.
We will go over the following topics one by one:
- The impact of security breaches
-
Traditional Network Architecture
-
How does Zero Trust work?
- The main concepts of Zero Trust Architecture
- Is Zero Trust by itself enough to protect your network?
- What are the best practices for securing networks?
Recent cyber-attacks made it clear – it’s time for Zero Trust. Unlike perimeter-based security, which makes it harder for a potential hacker to traverse through internal core systems, Zero Trust assumes hackers are already inside your network.
The Impact of Security Breaches
Earlier this year, in what appears to be the largest cyberattack on an American energy organization ever, a group of hackers breached the Colonial Pipeline network using a leaked password they found on the dark web. Using the compromised password, they were able to traverse through Colonial’s critical network systems, leading to a complete shut-down of the entire pipeline that resulted in fuel shortages across the USA East Coast. After stealing nearly 100 GB of Colonial’s data and threatening to leak this information, the Russia-based hacker group known as DarkSide got paid $4.4 million.
A great article by Lorance Abraham from Bleeping Computer shows how the Pysa ransomware organization used a simple PowerShell script to get the information they look for after gaining control of an organization’s Domain Controller. Once a hacker gains control of a Domain Controller – game over. From this point, all a hacker needs is a simple PowerShell script to search for files related to the company’s financial information, banking information, login credentials, and insurance policies. Once a hacker gets a hold of this type of information, they assume an organization will pay ransom to not spread the information.
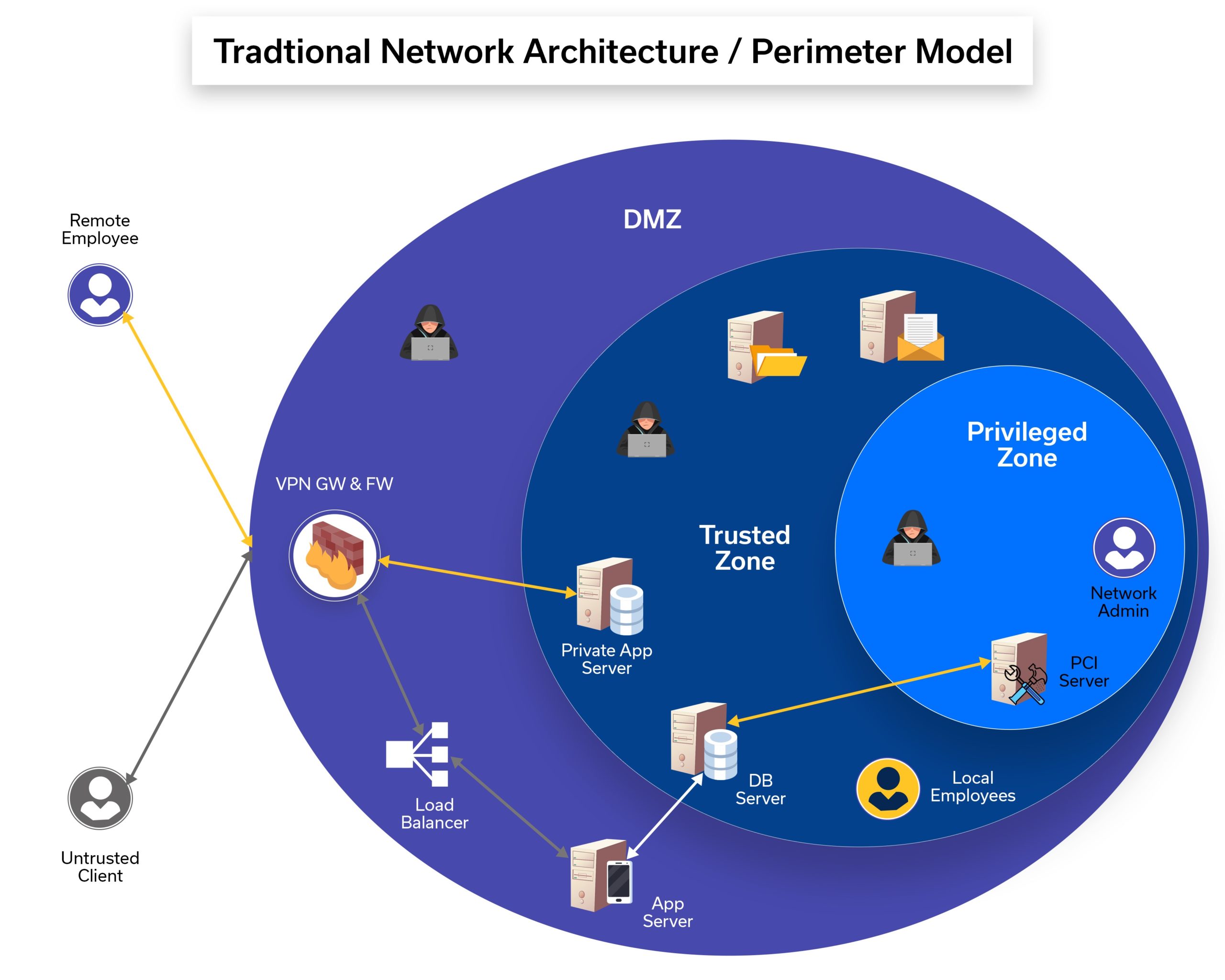
The Challenge of Traditional Network Architecture
Traditional network architecture is a perimeter-based network, which is widely used but cannot prevent different types of hackers from accessing a sensitive organization’s data or gaining control of critical systems. Until now VPN solutions were used in securing network communications and preventing untrusted access to sensitive data. However, although capable of securing communication channels using data encryption, VPNs are useless in preventing security breaches if an attacker gets hold of credentials to a network.
ZTA on the other hand, with its strong authentication and authorization capabilities, is the ideal solution for this major security concern.
Learn why VPN security is not enough to protect your network
Image: Traditional Network Architecture Model
It’s time for Zero Trust!
Organizations’ security leaders understand now that Zero-Trust has become the top cyber security priority, due to the recent high success ratio of cyber-attacks. 96% of security decision-makers who participated in Microsoft’s 2021 Zero Trust Adaptation Report stated that Zero Trust is critical to their organization’s success. 76% are in the process of implementation already. 73% expect their Zero Trust budget to increase.
How Does Zero Trust Work?
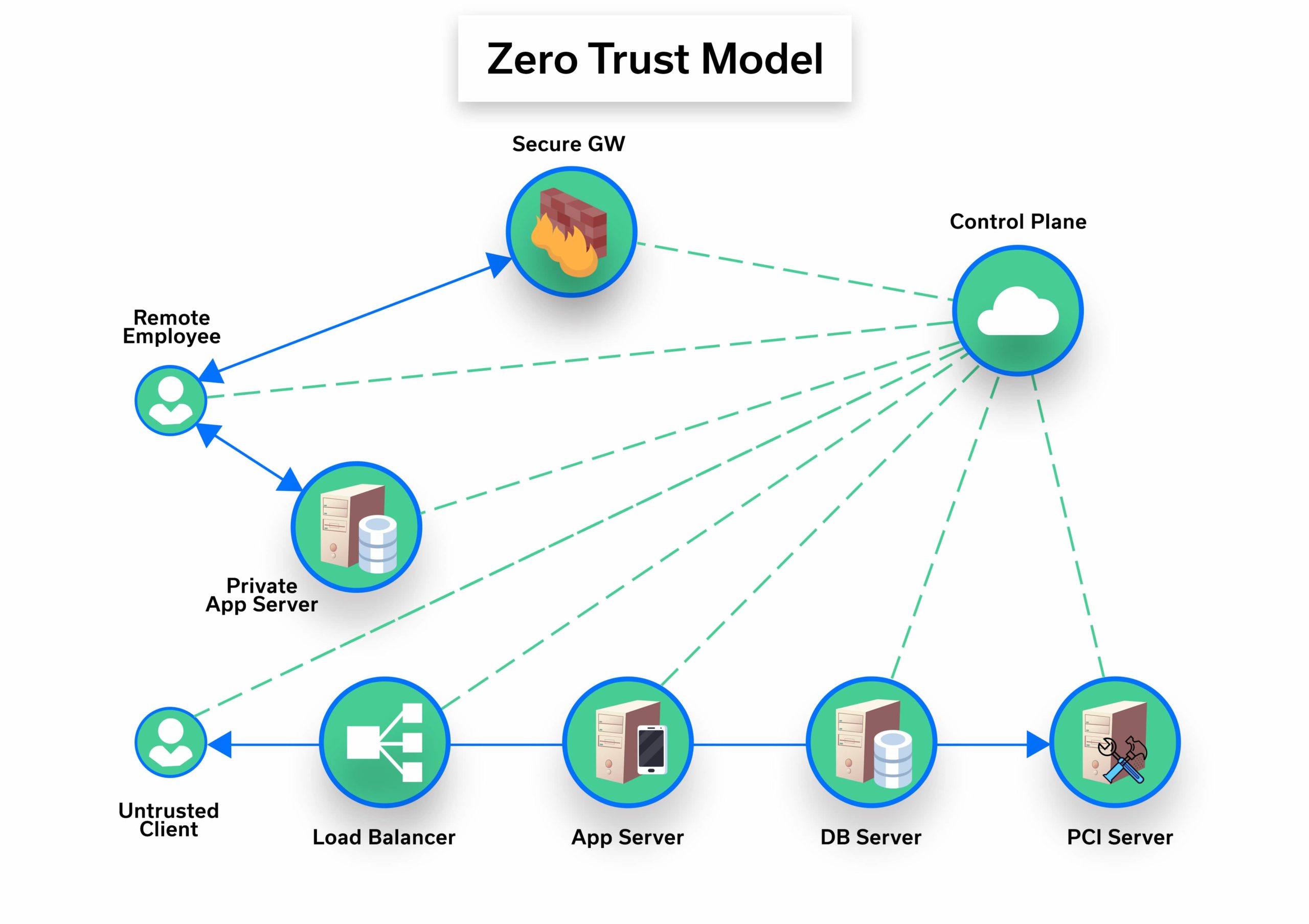
A zero-trust network is just as it sounds – i.e., a network that is completely untrusted. We interact with such a network very frequently – the Internet. Instead of breaking a network into location-based pieces, if we declare that network locations have no value, VPN suddenly is not needed (along with several other modern network constructs).
Zero trust is about minimizing the trusted zones and separating systems so that each one does its own authentication and authorization.
Image: Zero Trust-Based Network Architecture Model
The Main Concepts of Zero Trust Architecture:
-
Trust No One. The Zero Trust paradigm works on the principle that every network component is untrusted by default, inside or out. An additional authentication layer is needed. Privileges to users are given only after multiple authentication processes and only if allowed, depending on their function within the organization.
-
Individual authentication and authorization. Since every user and every request is individually checked and authorized, even if attackers gain access to an enterprises’ premises or even hack into a system, they won’t be allowed to get any further information/control for free.
-
The Importance of the Control Plane. The Control Plane is where the authorization decisions take place for every access request in the network, for all devices and users.
-
The Need for a Security / Access Policy. The security/ access policy is applied at this stage, based on an individual’s function within the organization, the time or date, or even the type of the device (for example, if an employee tries to connect a resource from their personal smartphone they need to provide explicit (dynamically changed / static) unique authentication data (token) which only that user knows about. (This eliminates the possibility of a hacker gaining access in case the smartphone is compromised.)
-
Automatically Set Permissions. If a request to a resource is allowed by the control plane, it automatically sets permissions to accept traffic from that client to that specific resource. The control plane may also instruct the network entities for the encryption details of this request.
The main concept here is that one entity (the control plane) is in charge and instructs the network components of all authentication and authorization processes, as well as coordinating all needed access settings automatically, with no delay, once all authentication credentials are provided.
So is Zero Trust Alone Enough to Protect your Network?
No. Imagine for a moment the outcome of attacking a Zero Trust model-based network with DDoS attacks. What would happen if the Zero Trust control plane is not protected against DDoS attacks?
Why Zero Trust Cannot Prevent DDoS Attacks
The truth is, if these types of DDoS attacks succeed in taking down the Control Plane components in a ZT based network, making it unavailable for new requests, the entire network becomes unavailable, and no one gets access to any part of the network. As specified in NIST Special Publication 800-207 section 5.2, this is a major weakness – and considered a serious security risk organizations must consider and prepare for.
What are the Best practices for Securing an Organization’s Network?
The best solution for securing a network is implementing a ZT solution alongside well-designed DDoS protection. A Zero Trust solution protects an organization from security breaches to sensitive systems and information, while DDoS protection validated 24/7 keeps the organization’s online services and Zero Trust components protected and available, ensuring new requests to resources are handled by the Control Plane.
MazeBolt’s patented RADAR™ testing validates that your network is well protected against DDoS attacks by testing more than 100 different DDoS attack vectors against every target in your network, without any disruption to your production environment. RADAR™ testing is used by top financial organizations, governments, and e-commerce companies to make sure their DDoS protection is constantly updated with the latest changes in the network and latest DDoS trends.
Reference:
https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RWGWha
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207.pdf