DDoS attacks aren’t a matter of if, they are matter of when. It’s simply a matter of when they decide it’s your turn to be attacked – whether they are mad that your end-of-year sale didn’t include the new technology they wanted; you’re doing business with a company or country with which they don’t approve; or they want to distract you with a major DDoS attack while they steal your crown jewels.
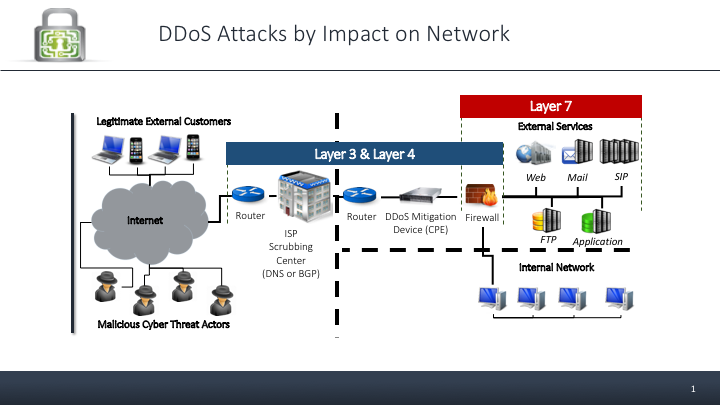
These three layers are the key targets for DDoS attacks: Layer 3, Layer 4, and Layer 7
- Layer 3 deals with traffic flow, IP addresses and routing.
- Layer 4 covers how end-to-end communication is governed, tracks active network connections, and allows or denies traffic based on the state of the sessions.
- Layer 7 is the application layer, e.g. web and mail, is concerned with the content of the data packets.
No matter the motive, while DDoS attacks come in many permutations and combinations, the three most common attacks are Volumetric, Protocol, and Application. Volumetric and Protocol attacks generally go after Layers 3 and 4 in your network, and Application layer 7 are attacks on your application E.g. Web or Mail.
Volumetric attacks (Generally Layer 3 and 4), generate massive amounts of traffic and basically clog the bandwidth and slow web or other service performance, ultimately preventing access to your website or service. The size of the attack is measured in bits or packets per second. An attack against GitHub is the largest attack on record, with an estimated 1.35 Tbps at its peak.
Volumetric attacks are the simplest to create, so they are most common. Simple amplification and reflection can be used to transform a small amount of traffic generated by the hackers into massive volumes.
Protocol attacks (generally Layer 4) use up all the processing capacity. For example, saturating an end server’s CPU or connection table using a connection-oriented attack quickly overwhelms the ports and resources needed for legitimate clients to connect to the service.
Application attacks (Layer 7) exploit weaknesses in your application layer, overwhelming the database or server powering the application directly. They are the hardest to identify and mitigate because it’s hard to identify human traffic from bot traffic. A lot of these new attacks are using the same “latest” technologies as everyone else – machine learning, AI, and behavior – to disguise their attacks.
Some of these attacks are easier to stop than others, but no matter how good your system may be, if it hasn’t been configured properly for your specific environment, it will fail.
MazeBolt can test all your systems at every layer to discover what you need to do to protect yourself.
Forewarned is forearmed. Download our information sheet about all the attacks that will be coming your way.
Sources
- https://www.us-cert.gov/sites/default/files/publications/DDoS%20Quick%20Guide.pdf
- http://www.idconline.com/technical_references/pdfs/data_communications/The_difference_between_layer_2_3_and_4_network_switches.pdf
- https://en.wikipedia.org/wiki/Denial-of-service_attack#Application_layer_attacks
- https://www.wideband.net.au/blog/difference-layer-3-layer-2-networks/
- https://serverfault.com/questions/792572/what-does-a-layer-3-4-firewall-do-that-a-layer-7-does-not
- https://devcentral.f5.com/articles/layer-4-vs-layer-7-dos-attack
- https://www.cybrary.it/0p3n/intro-common-layer-3-layer-4-layer-7-dos-attacks/