Understanding DDoS Testing and its importance in today’s security landscape
DDoS attacks and the ensuing challenges such as downtime, loss of revenue, and customer goodwill, have created a niche for DDoS testing as an exclusive, mandatory security requirement.
The importance of DDoS testing can be understood in a blog that GitHub put out in 2014 after it suffered a massive DDoS attack that saw incoming traffic at a rate of 1.3 Tbps. The DDoS attack which went on for over 2 hours, made GitHub completely unreachable.
This painful attack, according to GitHub, was mitigated. However, the damage had been done in spite of mitigation postures. This paved the way for transformation, and GitHub investigated ways to simulate attacks in a controlled environment, to test their countermeasures. They invested in testing on a regular basis to build additional confidence in both their mitigation tools and to ensure improved response time going forward. To summarize, GitHub would rely on testing and automation to ensure resilient infrastructure.
However, in 2018, four years later, GitHub suffered the biggest DDoS attack to date. At its peak, this attack saw incoming traffic at a rate of 1.3 terabytes per second (Tbps), sending packets at a rate of 126.9 million per second.
Understanding why DDoS Testing could not prevent further attacks for GitHub requires a basic understanding of how DDoS Testing works.
DDoS testing follows four steps:
Scoping: The Test Plan template is designed during this starting phase where all that needs to be protected including 3rd party applications are identified. The template includes necessary information with regard to countermeasures and identifies roles and lines of responsibility. The template is circulated to all concerned.
Design: The targets are analyzed from the attacker’s point of view and target profiles are created. This helps to uncover variations in attack format and helps to create the test plan.
Implementation: The tests are created in the testing platform and parameters will be entered and tested at low levels to ensure that all risk factors are considered.
So why is DDoS testing NOT a complete solution to ensure DDoS mitigation effectiveness?
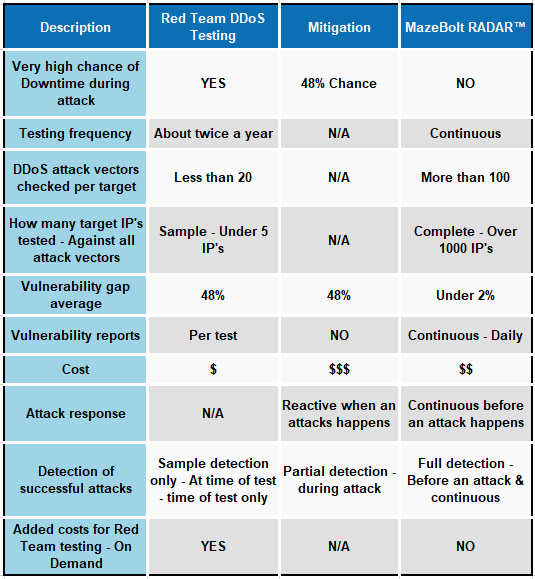
Testing is invariably performed around twice a year. As static tests, it is done on dynamic environments that are constantly changing due to website upgrades, new applications, etc. hence their conclusions are not timely and do not hold well for extended periods of time (generally less than 1-2 months).
Some of the other challenging factors that need to be kept in mind are:
- DDoS testing’s capability to detect DDoS risks before attacks are limited
- During testing, there will be disruption to ongoing operations
- The number of DDoS attack vectors covered is less than 20
- Coverage of Web-facing IP Addresses is normally limited to around 4.
- Vulnerability re-validation is limited to once a year, leaving the organization vulnerable for the rest of the time.
- Finally, there is no proactive DDoS security.
Additionally, the key factor before or during an attack is the human factor. The security engineers, when busy battling an attack, will not be able to monitor other activities creating a `blind spot’ which DDoS actors can exploit to penetrate the organization.
The DDoS Vulnerability Gap
A DDoS vulnerability gap occurs whenever DDoS traffic bypasses a company’s DDoS mitigation defenses to penetrate the target network causing system disruption and downtime.
MazeBolt’s RADAR testing closes the gap through continuous identification and remediation of the mitigation system’s vulnerabilities and not just the human readiness for an attack. Its proactive approach eliminates inline mitigation vulnerabilities before an attack happens, without any need for downtime (i.e. disruptive maintenance windows).
RADAR™ testing, MazeBolt’s new patented technology solution, tests for DDoS vulnerabilities continuously and non-disruptively. It delivers advanced intelligence with simple reports on how to remediate the DDoS vulnerabilities found. RADAR™ testing assists organizations in achieving, maintaining, and verifying the continuous elimination of their DDoS vulnerability gaps. This reduces — and maintains — the DDoS vulnerability gap from an average of 48% to under 2%.
Here is a quick reference chart comparing traditional DDoS testing and MazeBolt’s RADAR™ testing: