So we know cybercriminals are targeting us on account of the abundance of personal information available on the internet (Post #1), and we can smell a bogus email address or domain name a mile away (Post #2), but what guidelines help us identify a rogue link when we see one? And what are common link–clicking pitfalls to avoid?
Before diving into links, let’s step back and take a broader look at the phishing attack landscape so we know what to expect and where.
The following are three popular types of phishing attacks we’re seeing:
Spear Phishing: Cybercriminals profile a target, that may be a person or group of people in a company, and use publicly available information to craft a Phishing Campaign based on personally relevant work or social details. Example could be an email from your online shopping vendor just before the holidays claiming ‘missing payment’ details, or an executive in your company with a ‘new official procedure’ for review. This type of attack shows a high level customization of the phishing email to the recipients.
Chat Phishing: Cybercriminals manipulate chat sessions by either creating fake profiles or hijacking existing accounts to lure friends of the compromised account to click on malicious links and disclose sensitive information.
Water Hole Attacks: Cybercriminals plant malware on websites most likely to be visited by the campaign’s targets. These websites when visited will attempt to infect the visitors’ computer via a vulnerable browser or vulnerable plugin the user is running in his or her browser.
Now, let’s have a closer look at those links.
Links are essentially references that allow a user to access other documents or open programs by clicking on them. Links come in two forms: Text links and Image links, in both case – the visible text and image contain an underlying URL which refers to the target site.
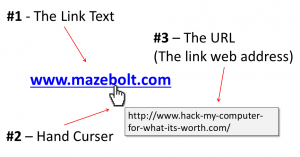
The good news is that whichever form they come in links are always very visible and easy to examine. (See image 1 for Key link components) by HOVERING over the link WITHOUT clicking it you can:
Image #1: Key link components
(i) See a change in curser type (from the arrow to the hand curser) to indicate the link, and
(ii) See the underlying URL (the web address the link refers you to) in a dedicated popup window or in the status bar on the bottom of your screen / web browser.
As is always true for Phishing, what you want to be looking for is inconsistency. These are some of the more common pitfalls to look out for when examining a link:
1. Lookalikes: These are text links that look like a legitimate URL as highlighted in Image 1 above. Note that for text links the Link text and link URL do not need to be the same! Even if the link text looks like a legit URL ALWAYS examine the underlying URL to make sure the site you are being directed to is consistent with the one you expect.
2. Ummm, I don’t think so!: Just because you’re asked to click a link doesn’t mean it makes sense to do so!
Email invitations to access online accounts via links should always trigger that sense of healthy paranoia and be examined carefully. As a rule, always access online accounts from their official website – NEVER from a link in an email. An exception would be when you have reset a password or initiated an email verification process yourself. If you think the email is authentic and requires your attention – access your on-line profile from the official website.
3. Cool! Huhaha!: Chat Messages, or posts on Social Media, from friends inviting you to “check out the latest!, coolest!, most outrageous!” are very common, but before clicking away, check with the friend that they actually sent it – cybercriminals will most likely not be there to answer your verification.
4. IP Addresses: Every website URL address also has a numerical label know as its IP address. When links are presented in this format you do not know where you are being redirected to. If all else looks legit, we recommend double checking with the email’s sender that it is.
The last post in this series ‘Phishing Commandment #4: Unshare Thyself’ will start with simple measures you can take on social media to manage your public exposure and end with the main takeaways from the series to help you reestablish trust in digital communication alongside your newfound awareness.