The first post in this series explained how phishing has evolved from the early spam based campaigns into far more sophisticated and subtle attacks that manipulate the individual’s publicly available personal information. The post recommended adopting a healthy paranoia towards emails and digital communications in general.
Ok, ok, we’re paranoid! But what do we do now?
Cybercriminals can only execute their devious plans if you act on their emails in one of two ways:
(i) Click on a malicious link, or
(ii) Open a malicious file
Doing either of these allows cybercriminals to install malware onto your computer, this allows a cybercriminal to potentially: steal data, access your microphone and speakers, steal credit card information, utilize your machine in a more advanced attack against other targets in your network and many other criminal activities they think up!
Therefore, ANY email REQUESTING AN ACTION should ring an alert bell!
The first step in verifying an email’s authenticity is validating that the sender is indeed who they claim to be. This brings us to our second Phishing Commandment ‘Know Thy Email Address’.
In Figure #1 we’ve broken down an email address to its three main components. Part III.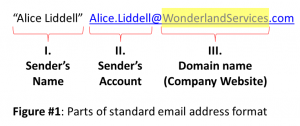
the email address’ ‘Domain Name’ (“WonderlandServices.com”) is always legally registered to the company that owns it (in this case Wonderland Services) and cannot be changed unless the company has been hacked into (which is the less common case and will be treated in the last post in this series).
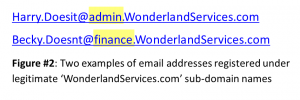
Once a company has registered a domain name it may add as many ‘sub-domains’ (or ‘Labels’) for internal usage such as the ‘admin’ and ‘finance’ examples in Figure#2. Without getting too deep into the Domain Name syntax, so long as the prefix or label is separated from the Domain Name by a dot (“.“) it’s legit.
Bingo!
Instead of trying to tamper with officially registered Domain and Sub-Domain Names, a much easier course of action for cybercriminals is to register a new Domain Name that LOOKS close enough to the original to pass as an official subdomain – but isn’t!
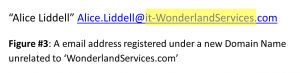
For example, Figure #3 we’ve added the prefix “it” using a hyphen (“-”) to the official ‘WonderlandServices.com’ that would imply it is a legitimate subdomain name of Wonderland Services’ IT Department.
But it isn’t.
You’d be surprised what you can get away with by hacking this domain name syntax rule! To see how easy it is to create a new domain that looks like it belongs to another company by adding a prefix preceded with a hyphen, go to any of the domain name registration sites (like www.godaddy.com) and try it yourself with one of the more popular companies you know.
Putting this back in context, with the abundance of personal information available online cybercriminals are able to launch attacks posing as real people using email addresses that look close enough to their official ones for colleagues not to notice. All a cybercriminal needs is one click on a malicious link to compromise a company’s network from which to advance their attack.
Remember: When in doubt, there is no doubt!
Stay tuned for our next post in this series: ‘Phishing Commandment #3: Know Thy Link’ that will help you understand what’s in a link and try to clarify how to identify malicious ones.



One Response
Thank you very much for sharing. Your article was very helpful for me to build a paper on gate.io. After reading your article, I think the idea is very good and the creative techniques are also very innovative. However, I have some different opinions, and I will continue to follow your reply.