It’s that time of year again… assessing your needs, clarifying goals, setting expectations and committing to budgets for next year!
When it comes to mapping DDoS risk, companies are starting to realize that DDoS mitigation (Equipment and scrubbing center services) is only part of their DDoS Risk Management Program.
The reason is, there’s usually a DDoS Mitigation Gap to close as well. But how do you measure your DDoS Mitigation Gap? and what considerations need to go into budgeting this critical piece of the DDoS Risk Management Program?
DDoS Mitigation Gaps
In a nut shell, a DDoS Mitigation Gap is the amount of traffic that gets through a DDoS mitigation system. In principle, companies with DDoS mitigation that’s sufficiently deployed shouldn’t have a DDoS Mitigation Gap. But due to the ever changing nature of companies’ networks with new services and servers being added all the time – in most cases the configuration of the DDoS mitigation posture isn’t fine-tuned to reflect these changes which opens gaps in the mitigation and lets malicious traffic through.
The main problem with DDoS Mitigation Gaps is that companies have little to no visibility on them and therefore before they can get their DDoS Risk Management Program budget right, they need to understand where and how big their DDoS Mitigation Gaps are.
Visibility on DDoS Mitigation Gaps
The most effective way to identify DDoS Mitigation Gaps proactively is DDoS testing. DDoS testing is an iterative process of simulating a wide variety of real DDoS attacks in a highly controlled manner to allow companies to determine where their mitigation is failing.
Based on data from hundreds of DDoS tests that MazeBolt conducted, companies that tested their DDoS Mitigation for the first time experienced an average failure rate (DDoS Mitigation Gap) of 48%. This means that companies that had already deployed mitigation are failing approximately 1 out of 2 DDoS attacks.
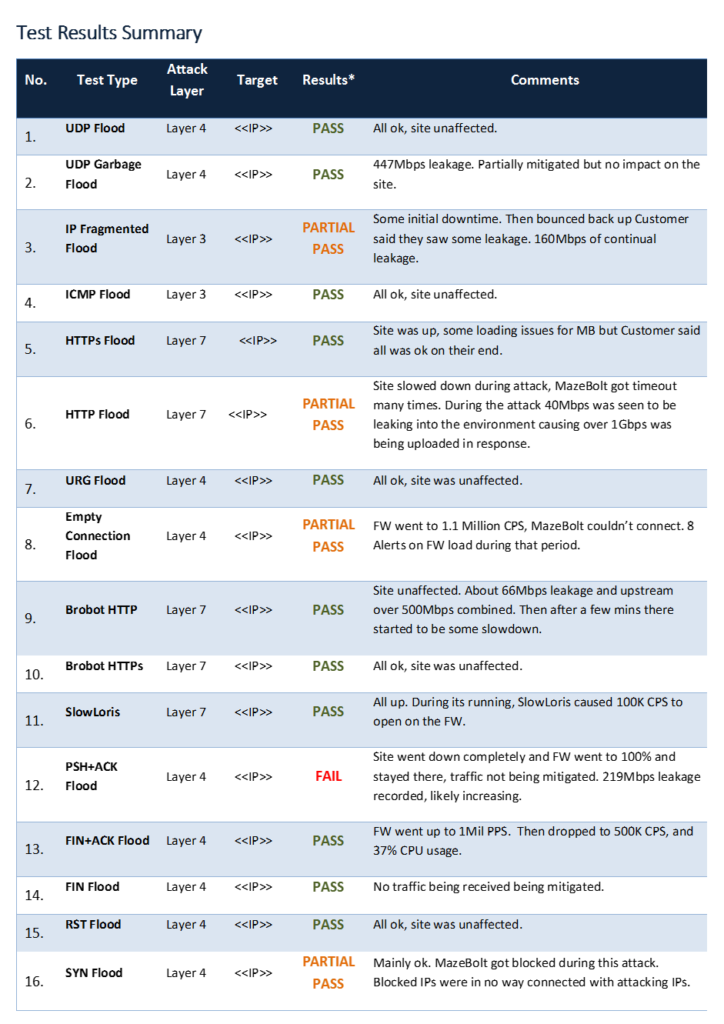
Engaging in a DDoS Risk Management Program provides companies with a much clearer understanding of where their DDoS Mitigation Gaps are and what is required to close them. (See Figure 1 – A Sample of MazeBolt’s DDoS BaseLine Testing Reporting Table)
DDoS Testing Considerations
Back to budgeting a DDoS Risk Management Program. The two main considerations a company needs to address in order to understand the scope of their annual DDoS Risk Management Program, are:
- Identifying critical services:
These are network services that if they were neutralized by a successful DDoS attack would significantly impact your ongoing operations. Some examples of such services may be: Web, VOIP & Mail servers. The significance here is that a DDoS Test can target only one such service at a time, hence the more critical targets a company has the more testing required.
- Bandwidth saturation:
With the size of DDoS attacks consistently increasing due to IoT based botnets, companies should assume DDoS attacks will be able to exceed their pipe’s bandwidth. This is why DDoS mitigation postures typically include a cloud scrubbing element that is able to absorb these gigantic volumes of DDoS traffic and filter it before it reaches the company’s network.
A DDoS testing program should be able test that the cloud scrubbing service is able to mitigate the malicious traffic at these high bandwidths.
Summary
Budgeting a DDoS Risk Management Program accurately, requires understanding your company’s DDoS Mitigation Gap (i.e. the amount of DDoS traffic bypassing your DDoS mitigation) and what it will take to close it. The most efficient way of gaining this insight and working to close the DDoS Gap is introducing DDoS Testing to your DDoS Risk Management Program. Clarifying the two DDoS testing considerations above will help you ensure your DDoS Risk Management Program’s budget suits your company’s needs.